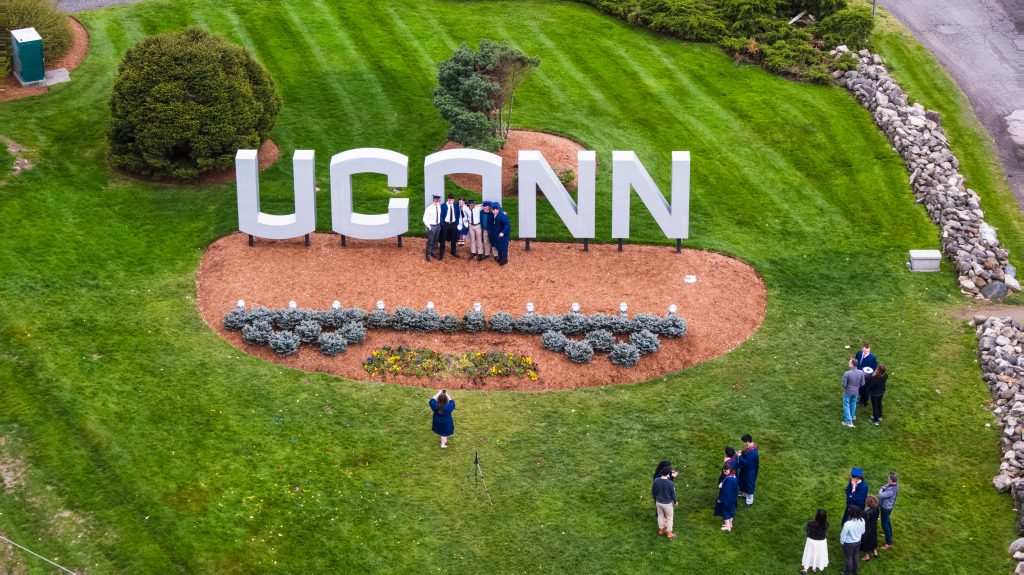College of Engineering
Celebrating UConn’s Class of 2024
The newest alums take their place in a great tradition
May 3, 2024 | Tom Breen
UConn Students Earn NSF Graduate Research Fellowships
The program supports outstanding students in NSF-supported disciplines who are pursuing research-based master’s and doctoral degrees
May 2, 2024 | Mike Enright '88 (CLAS), University Communications
UConn Army ROTC Training – Both in the Forest and Classroom – Prepares Students for Future
'There are very few people who aren’t interested in the things I’ve done. I mean, rappelling out of a helicopter, that’s just a good conversation starter'
May 1, 2024 | Kimberly Phillips
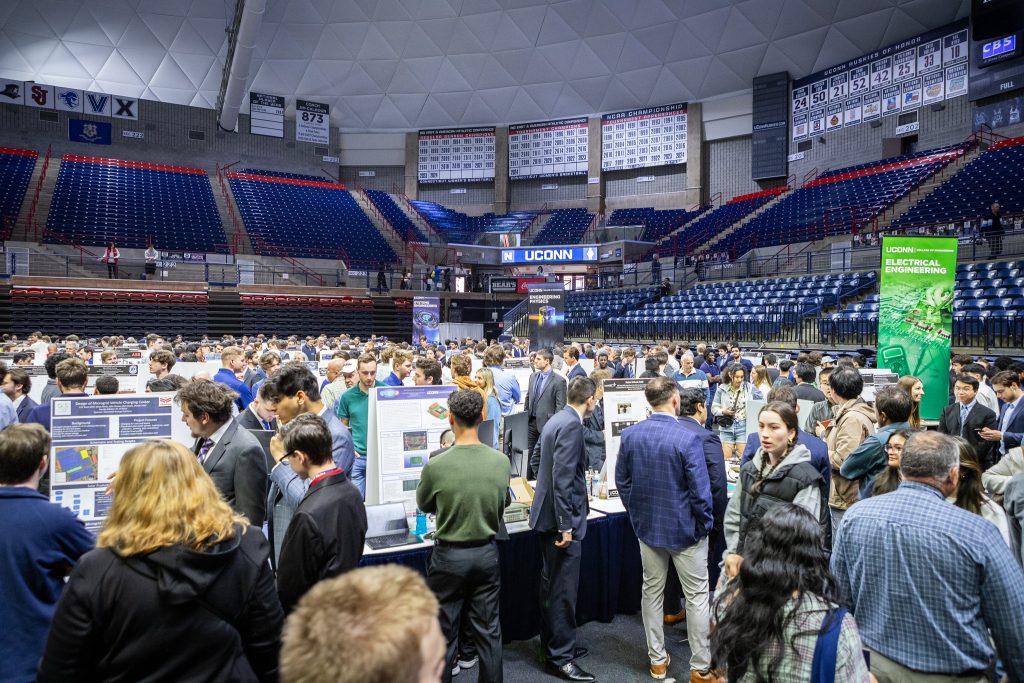
Engineering Students Share Yearlong Research Projects During Senior Design Demo Day
Through their Senior Design projects, students work to solve real-world engineering problems while learning valuable skills
May 1, 2024 | Olivia Drake
McCutcheon Uses Membrane Technologies to Engineer a Cleaner Future
This month, the North American Membrane Society (NAMS) is honoring College of Engineering Professor Jeffrey McCucheon for his outstanding contributions to the field of membrane science
April 30, 2024 | Olivia Drake
College of Engineering Launches New Collaboratory for Biomedical and Bioengineering Innovation
Biomedical and bioengineering researchers at UConn and UConn Health will work together to invent, develop, and establish new interdisciplinary collaborations outside their existing research networks
April 30, 2024 | Olivia Drake
DOE Grants Fund Collaborative Clean Energy Projects
UConn is one of dozens of beneficiaries in funding program to bolster research into hydrogen energy and related projects
April 25, 2024 | Matt Engelhardt
UConn Provost Announces Awards for Excellence in Community Engaged Scholarship
The Provost’s Awards for Excellence in Community Engaged Scholarship (PAECES) recognize scholarly activities that integrate community engagement with research, creative work, and teaching
April 24, 2024 | Briana Huett, Associate Director of Outreach and Engagement
Pratt & Whitney Engineering Building Unveiled
Pratt & Whitney has strong ties to the UConn College of Engineering and UConn School of Mechanical, Aerospace and Manufacturing Engineering
April 22, 2024 | Claire Tremont
College of Engineering Names New Dean
Ji-Cheng ‘JC’ Zhao brings 30 years' experience working in academia, industry, and government
April 19, 2024 | Claire Tremont